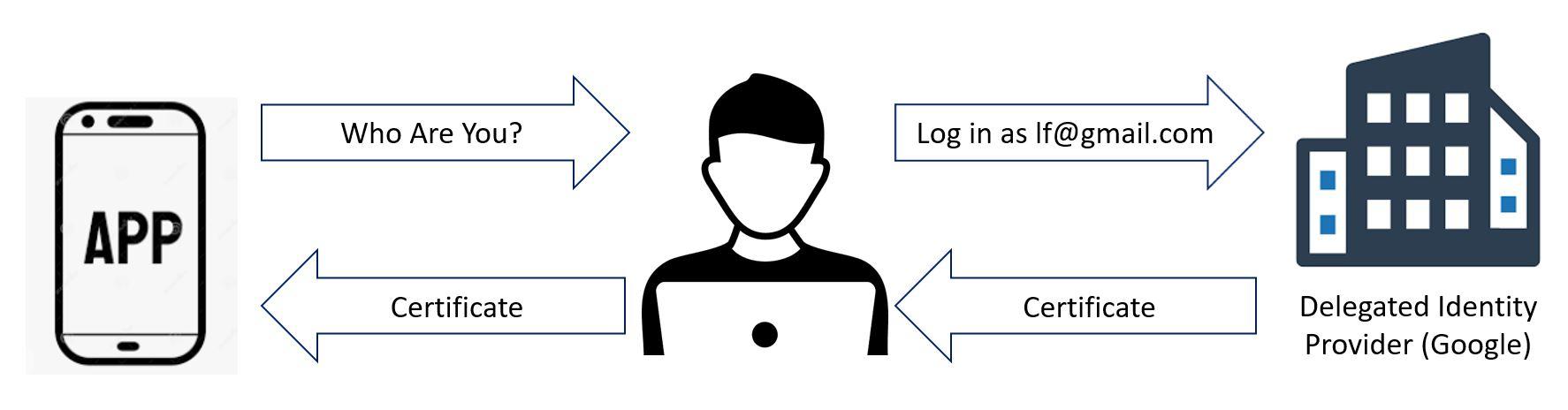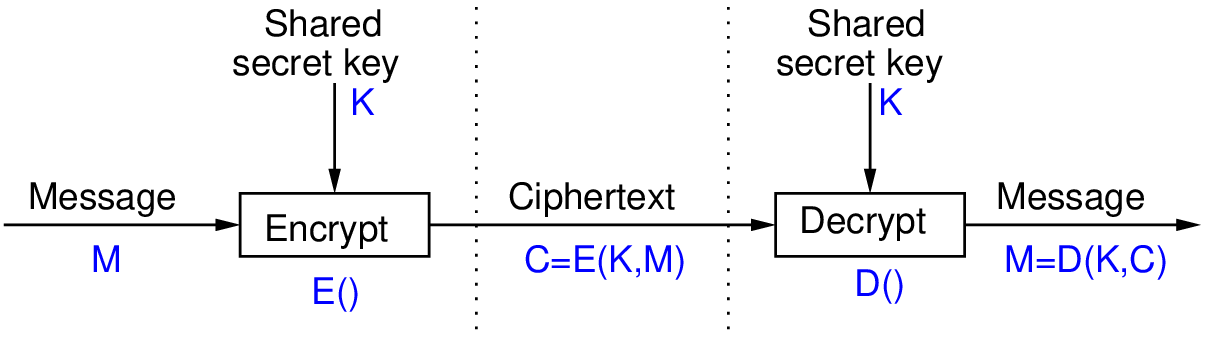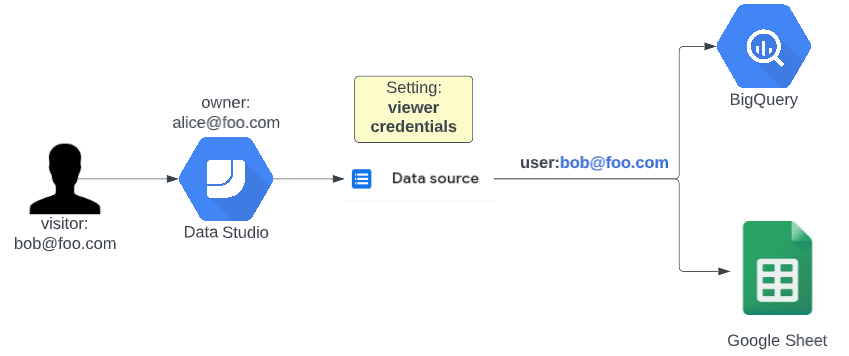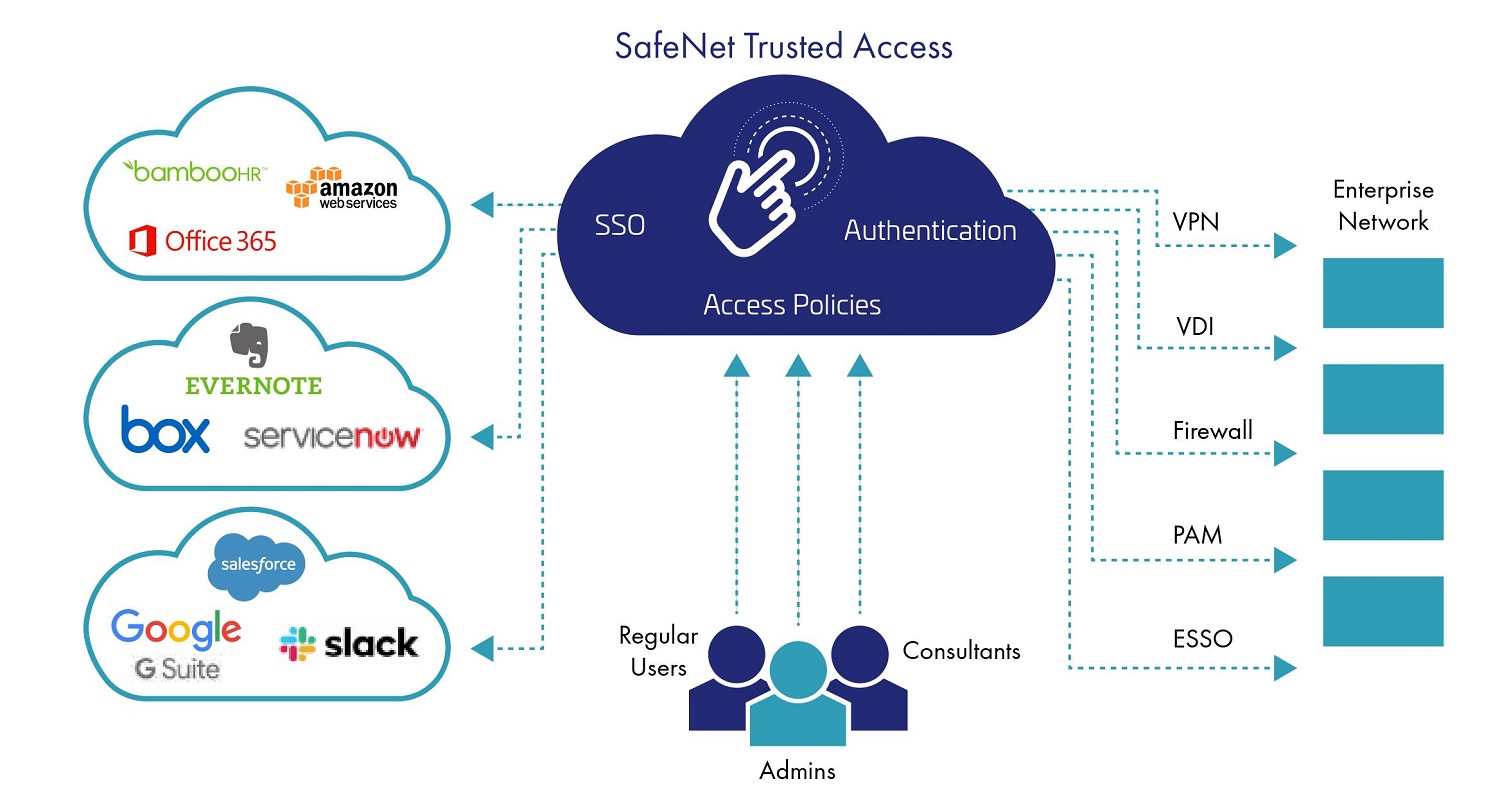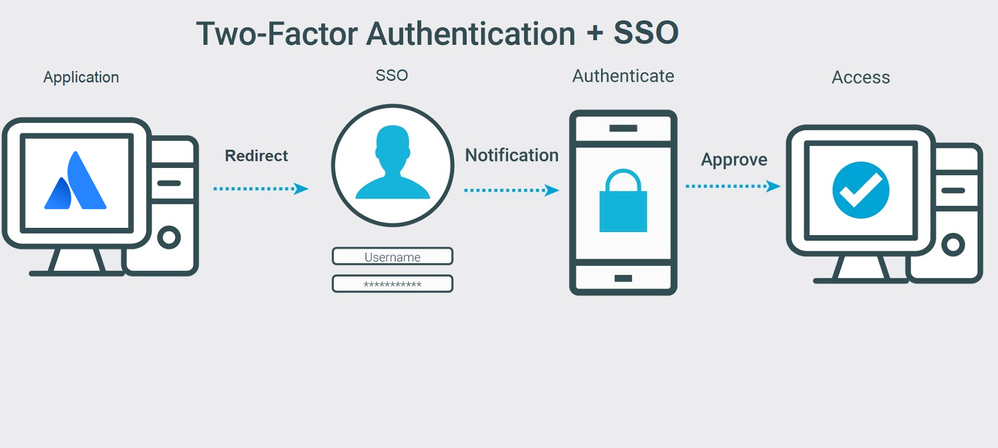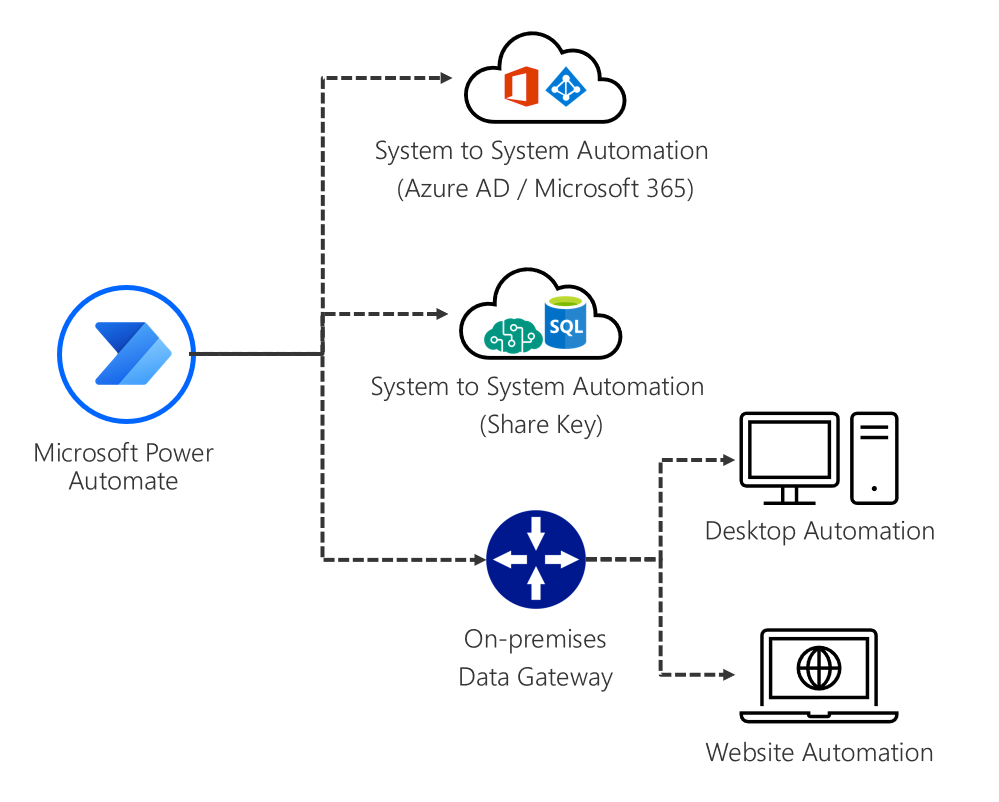
Authentication and security for planning a Power Automate project - Power Automate | Microsoft Learn

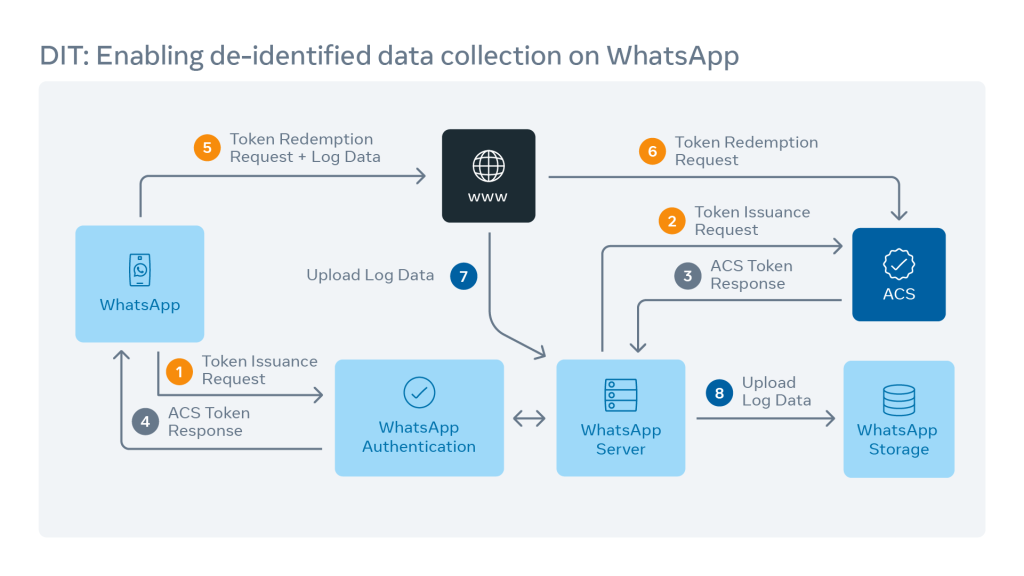
Subsurface Data Management: Overview of authentication and authorization on AWS implementation of OSDU™ Data Platform | AWS for Industries